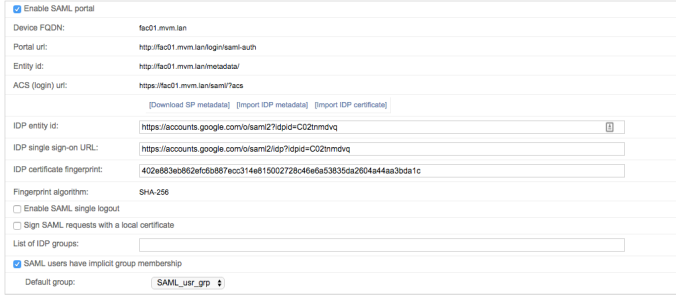
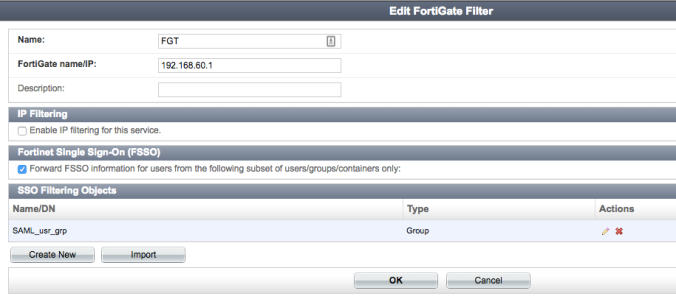
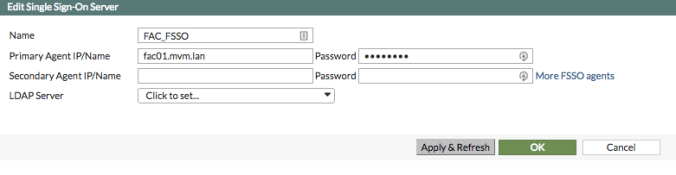
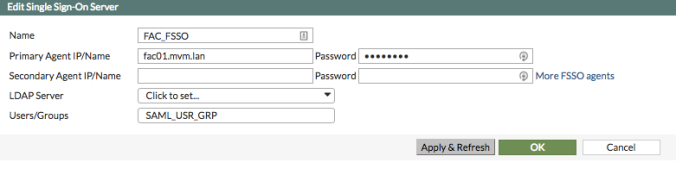
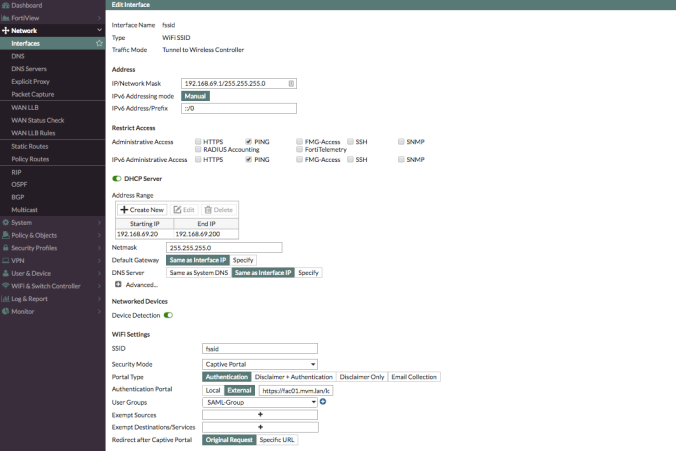
Goal
Check for presence of route 10.100.1.1/32 via peer with AS 4049.
If present, apply route map 60_30_ACCEPT_10_100. This will limit advertisements to peer 172.31.1.1 to strictly 10.100.0.0/8.
Prefix lists
config router prefix-list
edit "match_10.100.1.1_32"
config rule
edit 1
set prefix 10.100.1.1 255.255.255.255
unset ge
unset le
next
edit "accept_10.100/16"
config rule
edit 1
set prefix 10.100.0.0 255.255.0.0
set ge 24 // Also accept prefixes with a bitmask greater than 24, i.e /32
unset le
next
end
AS-path list
config router aspath-list
edit "match-as-4049"
config rule
edit 1
set action permit
set regexp "_4049_"
next
end
next
end
Route maps
config router route-map
edit "match-from-AS-4049"
config rule
edit 1
set match-as-path "match-as-4049"
set match-ip-address "match_10.100.1.1_32"
next
end
next
edit "60_30_ACCEPT_10_100"
config rule
edit 1
set match-ip-address "accept_10.100/16"
next
edit 2
set action deny
next
end
next
BGP configuration
config router bgp
config neighbour
edit "172.31.1.1"
set remote-as 64333
config conditional-advertise
edit "60_30_ACCEPT_10_100" // route map to apply
set condition-routemap "match-from-AS-4049"
next
end
next
Neighbour output – no match
BGP neighbor is 172.31.1.1, remote AS 64333, local AS 65531, external link
13 accepted prefixes
21 announced prefixes
Conditional advertise-map:
Adv-map 60_30_ACCEPT_10_100root, cond-map match-from-AS-4049root, cond-state 1-0
Neighbour output – match
BGP neighbor is 172.31.1.1, remote AS 64333, local AS 65531, external link
13 accepted prefixes
5455 announced prefixes
Conditional advertise-map:
Adv-map 60_30_ACCEPT_10_100root, cond-map match-from-AS-4049root, cond-state 1-1
1-0 means condition was not met; 1-1 means it was.
To soft-clear outbound routes
exe router clear bgp ip 1.1.1.1 soft out